Risk Management Enterprise Can Be Fun For Everyone
Little Known Facts About Risk Management Enterprise.
Table of ContentsTop Guidelines Of Risk Management EnterpriseThe 6-Minute Rule for Risk Management EnterpriseExamine This Report about Risk Management EnterpriseRisk Management Enterprise for BeginnersThe 6-Second Trick For Risk Management EnterpriseThe Basic Principles Of Risk Management Enterprise 7 Easy Facts About Risk Management Enterprise Shown
Below are some of its crucial features that centers have to know. So, have a look. Real-Time Danger Analyses and Reduction in this software program permit organizations to continually keep track of and examine risks as they progress. This feature leverages real-time data and computerized analysis to identify potential threats promptly. Once dangers are identified, the software application assists in prompt reduction activities.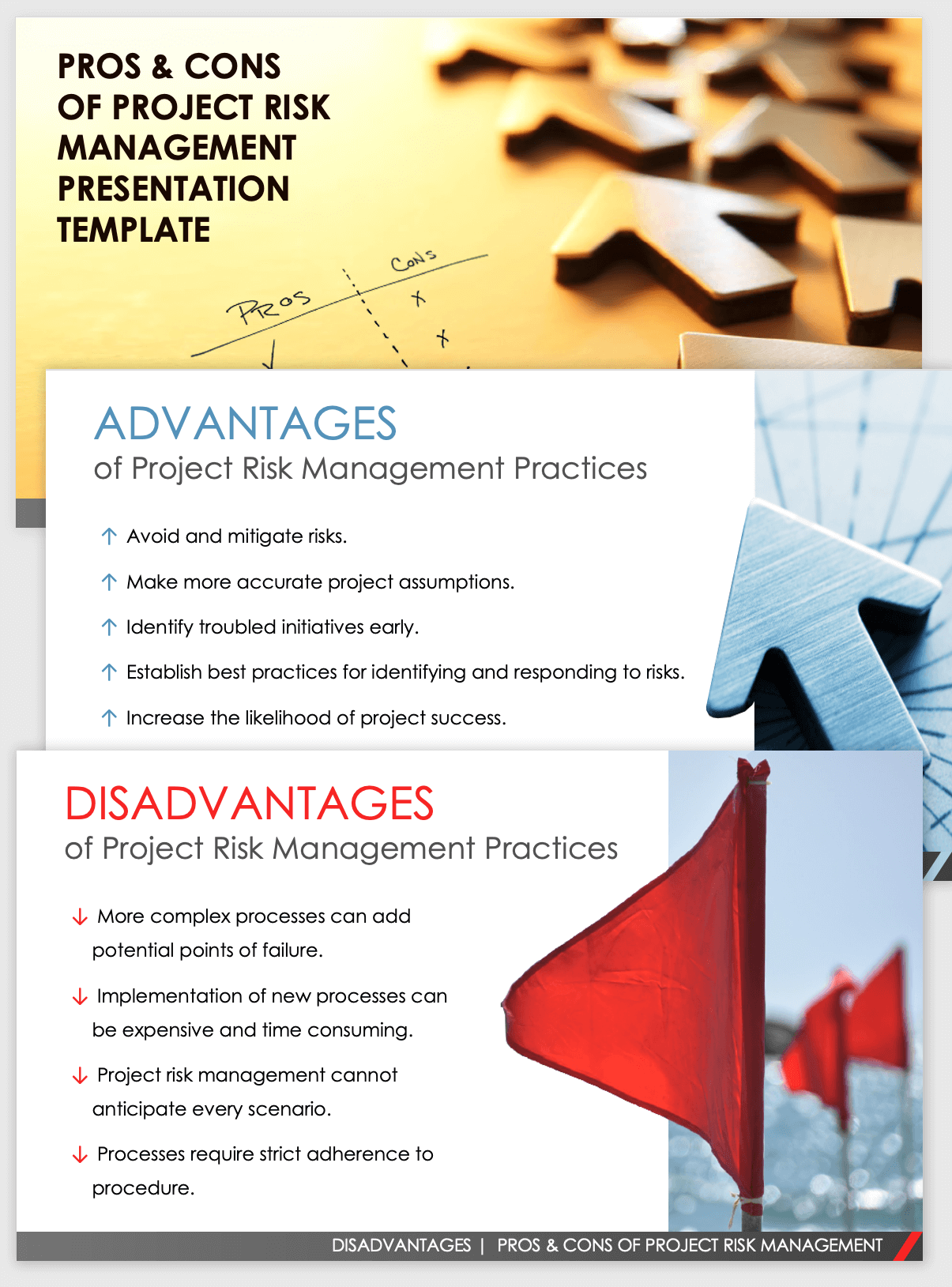
They deal with the obstacle of ongoing threat management by offering devices to keep an eye on threats constantly. KRIs improve safety and security risk oversight, making certain that prospective dangers are identified and taken care of successfully.
About Risk Management Enterprise
IT take the chance of administration is a subset of business risk administration (ERM), designed to bring IT run the risk of according to an organization's threat appetite. IT run the risk of administration (ITRM) incorporates the plans, treatments and innovation needed to decrease dangers and vulnerabilities, while preserving compliance with relevant regulative needs. In enhancement, ITRM looks for to limit the consequences of devastating events, such as safety and security breaches.
While ITRM frameworks provide valuable assistance, it's easy for IT groups to deal with "structure overload." Veronica Rose, ISACA board director and an info systems auditor at Metropol Corp. Ltd., suggests using a mix of structures to achieve the very best outcomes. As an example, the ISACA Danger IT framework aligns well with the COBIT 2019 framework, Rose stated.
Enterprise Threat Management Software Application Development: Advantages & Characteristics, Price. With technical improvements, threats are continuously on the increase. That being claimed, companies are most likely to encounter difficulties that affect their financial resources, operations, and reputation. From rapidly fluctuating markets to regulatory changes and cyber hazards, businesses navigate via a constantly altering sea of dangers.
The Risk Management Enterprise Diaries
In this blog site, we will study the globe of ERM software program, exploring what it is, its benefits, attributes, etc so that you can build one for your organization. Enterprise Threat Administration (ERM) software application is the application program for planning, guiding, organizing, and controlling service tasks and enhancing threat management procedures.
With ERM, companies can make informative choices to improve the general strength of the company. Read: ERP Application Growth Dedicated ERM systems are critical for organizations that routinely handle vast amounts of sensitive info and several stakeholders to accept tactical choices. Some industries where ERM has come to be a standard system are healthcare, finance, construction, insurance, and infotech (IT).
: It is demanding for any venture to undergo a comprehensive audit. Nevertheless, it can be stayed clear of by utilizing the ERM software system. This system automates policy compliance monitoring to maintain the organization safe and secure and certified. Aside from that, it likewise logs and classifies all the documents in the system making it much easier for auditors to examine processes a lot faster.
The Basic Principles Of Risk Management Enterprise
You can likewise attach existing software application systems to the ERM through APIs or by adding data by hand. Companies can use ERM to examine threats based upon their prospective impact for much better danger management and mitigation.: Including this feature allows customers to get real-time notices on their gadgets about any kind of threat that could happen and its impact.

Rather, the software program allows them to set thresholds for different processes and send push notifications in case of feasible threats.: By incorporating data visualization and reporting in the custom ERM software program, companies can obtain clear insights regarding danger patterns and performance.: It is compulsory for companies to follow market conformity and regulative criteria.
These systems enable companies to implement best-practice risk click reference monitoring procedures that line up with sector criteria, offering a powerful, technology-driven technique to recognizing, analyzing, and mitigating threats. This blog site checks out the advantages of computerized risk administration devices, the areas of threat monitoring they can automate, and the value they offer an organization.
The Definitive Guide to Risk Management Enterprise
Teams can establish up forms with the pertinent areas and easily produce different kinds for various risk kinds. These risk evaluation forms can be distributed for conclusion by means of automated process that send out notifications to the relevant staff to finish the forms online. If forms are not completed by the deadline, then chaser e-mails are immediately sent by the system.
The control surveillance and control screening procedure can also be automated. Firms can use automated operations to send normal control examination notices and team can go into the results by means of on the internet kinds. Controls can likewise be checked by the software program by setting guidelines to send notifies based upon control information kept in various other systems and spread sheets that is drawn into the system using API integrations.
Threat management automation software application can also sustain with danger reporting for all levels of the venture. Leaders can view records on danger exposure and control effectiveness via a range of reporting outcomes including fixed records, Power BI interactive reports, bowtie evaluation, and Monte Carlo simulations. The capability to draw live records at the touch of a button eliminates arduous information manipulation tasks leaving threat teams with even more time to evaluate the information and recommend the company on the best strategy.
Organizations operating in competitive, fast-changing markets can not pay for hold-ups or inefficiencies in addressing prospective dangers. Typical threat management utilizing hands-on spreadsheet-based processes, while familiar, frequently lead to fragmented data, taxing reporting, and a raised possibility of human error.
The Only Guide to Risk Management Enterprise
This guarantees risk signs up are always present and aligned with organizational objectives. Compliance is one more important driver for automating danger monitoring. Criteria like ISO 31000, CPS 230 and COSO all give support around risk monitoring ideal practices and control frameworks, and automated risk monitoring devices are structured to align with these demands helping firms to meet most commonly utilized danger monitoring standards.
Look for danger software program systems with a consents power structure to quickly establish process for risk rise. This capability allows you to tailor the view for each individual, so they only see the data pertinent to them. Make certain the ERM software supplies individual monitoring so you can see who entered what information and when.
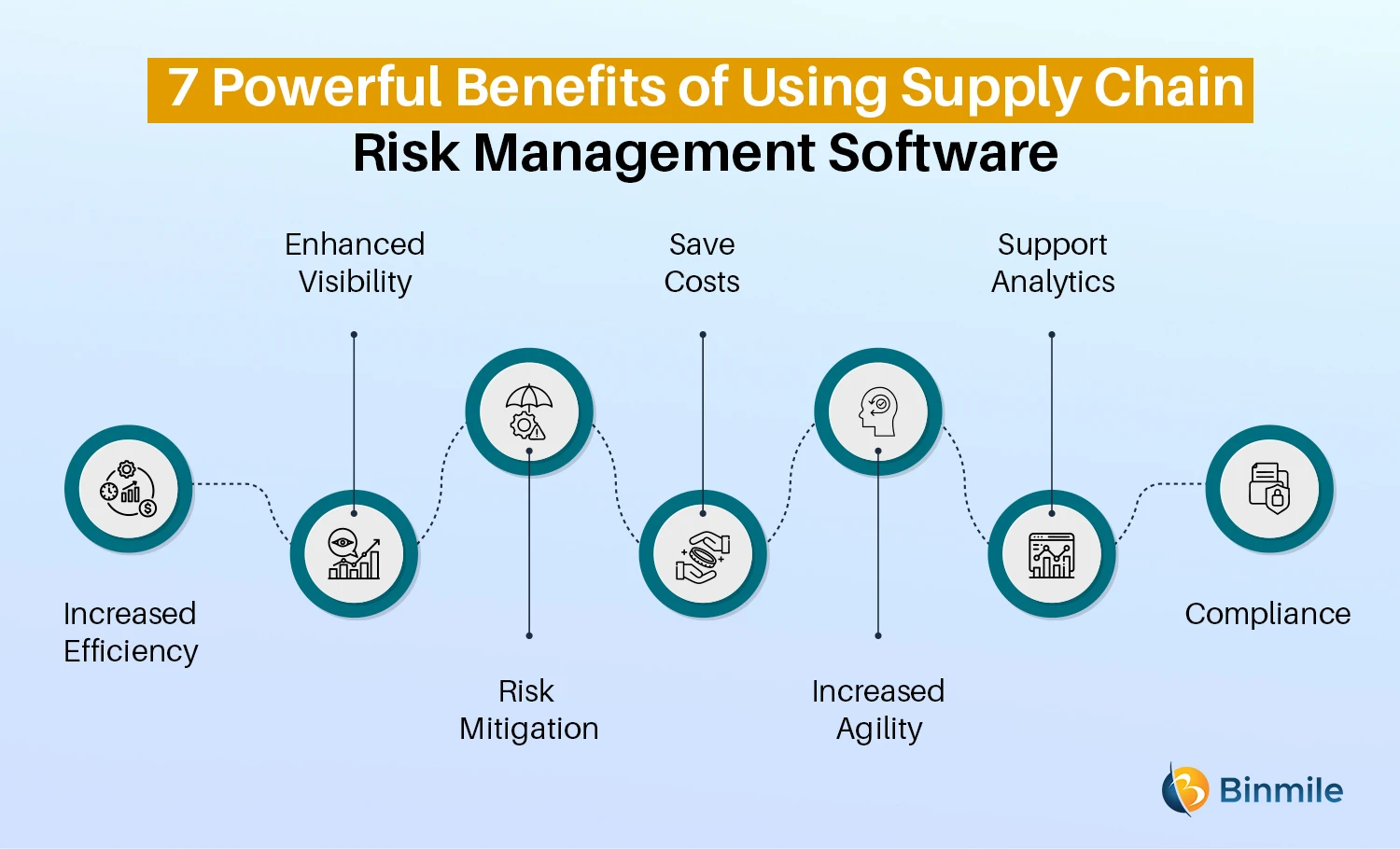
Go resource with a cloud-based platform to ensure the system gets normal updates from the supplier adding new capability. Seek tools that use job threat administration capacities to manage your projects and portfolios and the connected threats. The benefits of taking on threat management automation software application prolong far past performance. Businesses that integrate these options into their ERM strategy can anticipate a host of substantial and abstract.
Risk Management Enterprise for Dummies
While the case for automation is engaging, applying a danger management system is not without its difficulties. For one, information high quality is important. Automated systems count on precise, current info to deliver significant insights. To get over the difficulties of threat monitoring automation, companies should buy information cleansing and administration to make sure a strong foundation for executing an automated platform.
Automation in danger monitoring equips businesses to change their strategy to risk and develop a more powerful foundation for the future (Risk Management Enterprise). The question is no more whether to automate threat administration, it's just how quickly you can start. To see the Riskonnect at work,
The response frequently hinges on exactly how well threats are anticipated and handled. Project administration software works as the navigator in the tumultuous waters of project implementation, offering devices that recognize and examine risks and develop techniques to reduce them efficiently. From real-time information analytics to detailed risk tracking dashboards, these devices give a 360-degree view of the task landscape, allowing task supervisors to make educated decisions that maintain their tasks on track and within budget plan.